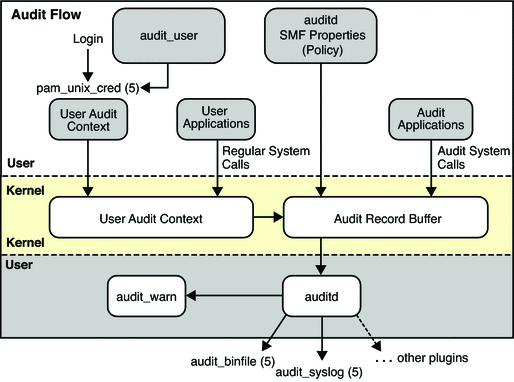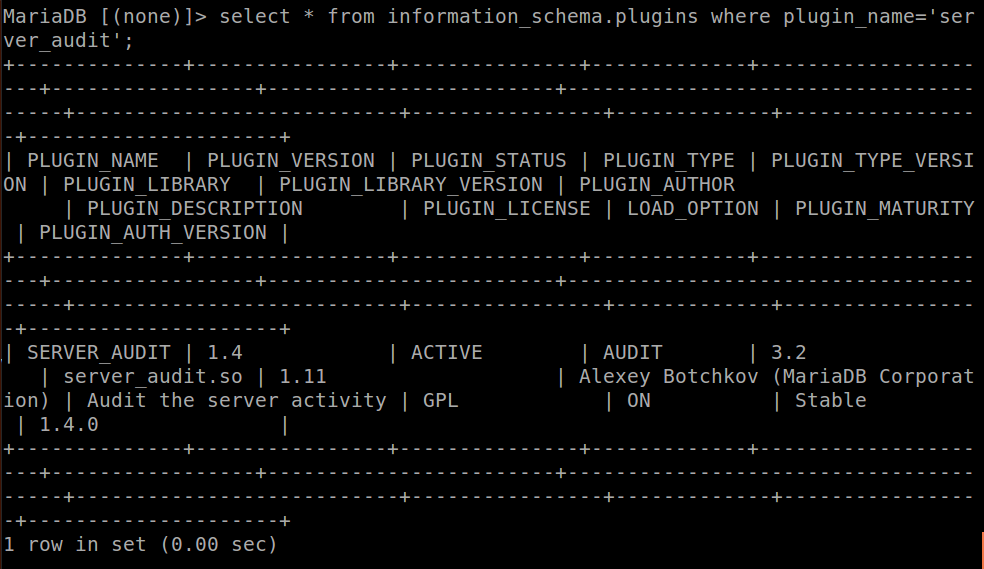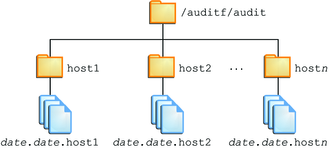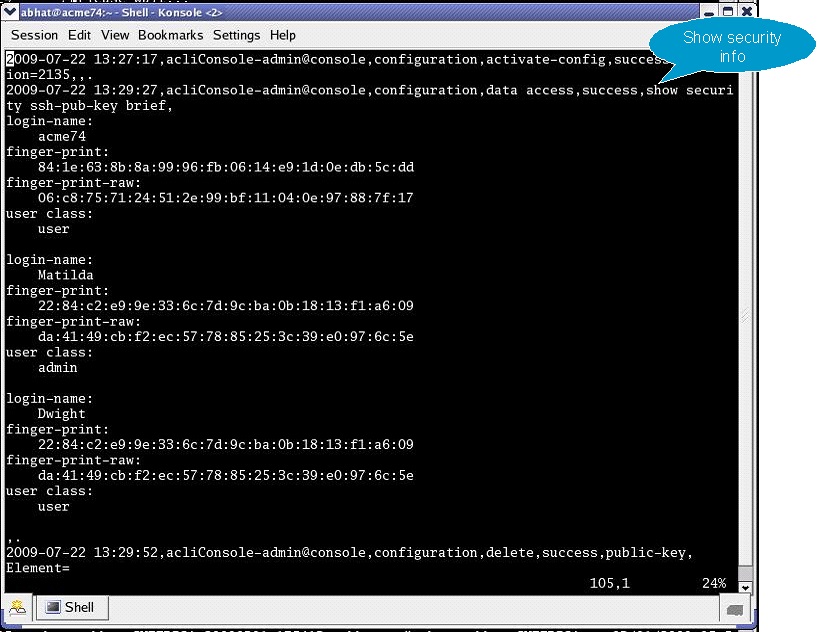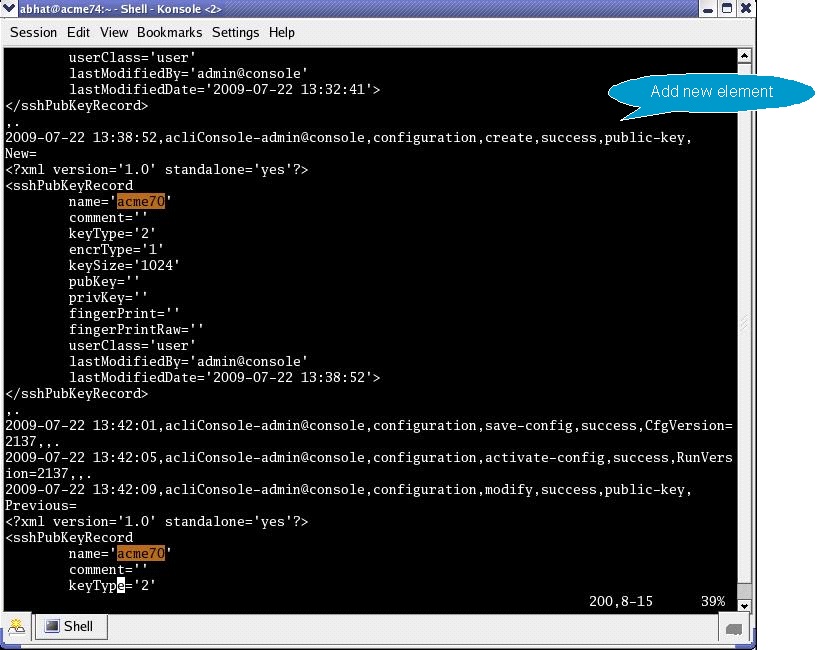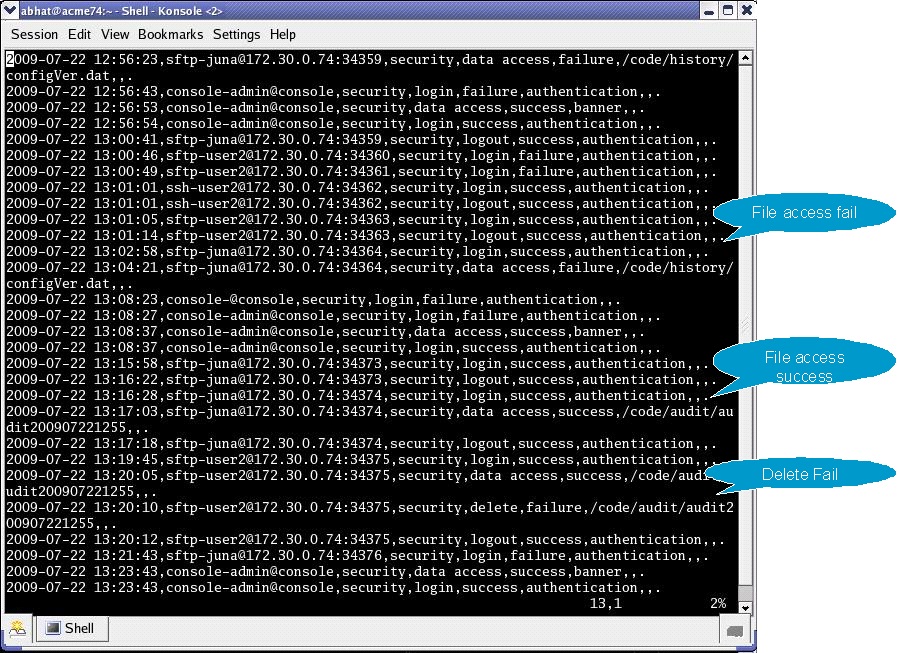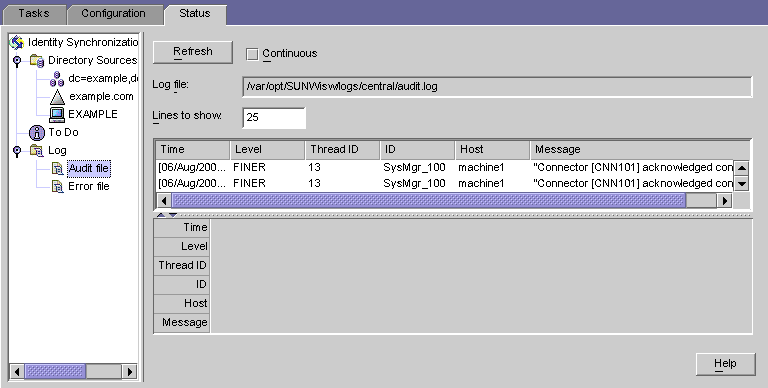
Chapter 11 Understanding Audit and Error Files (Sun Java System Directory Server Enterprise Edition 6.3 Installation Guide)

Solaris audit facilities and placement opportunities for pseudonymizer... | Download Scientific Diagram
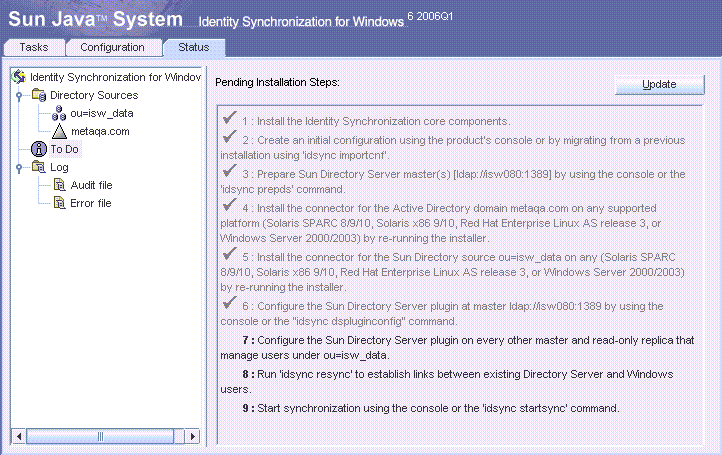
Chapter 9 Understanding Audit and Error Files (Sun Java System Identity Synchronization for Windows 6.0 Installation and Configuration Guide)